Managed Service Accounts (MSA) are intended to run as a service and not to be used by an end user to logon interactively; however, there are some cases where it is necessary for troubleshooting.
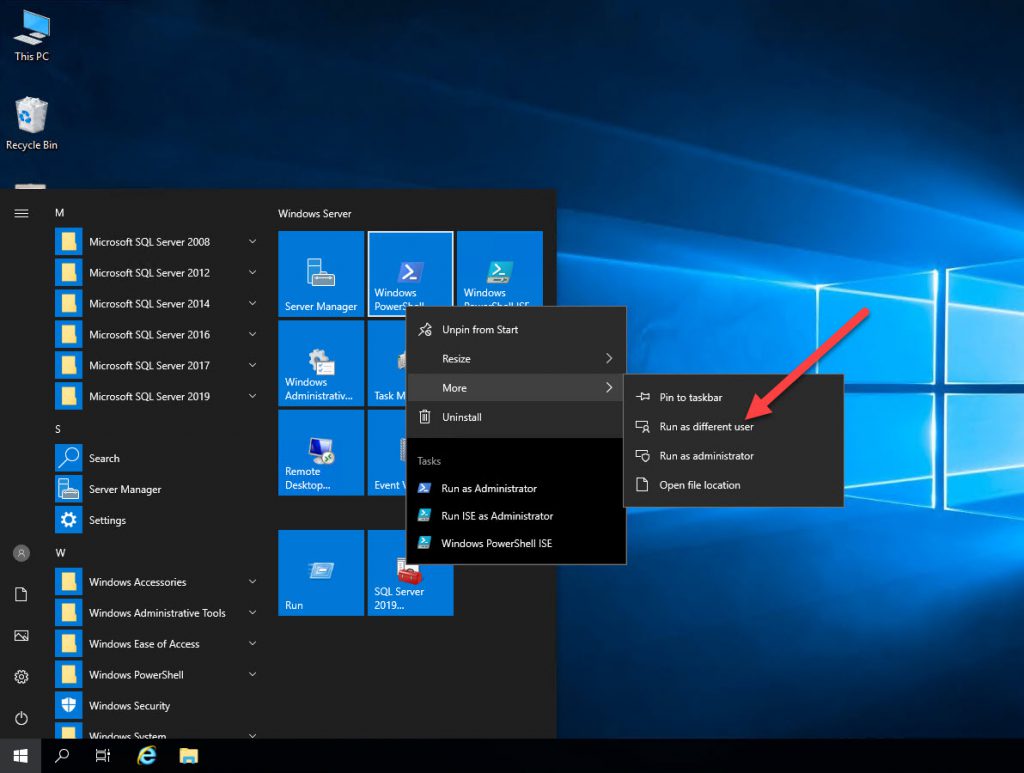
From the Start Menu, if you right click on the PowerShell icon, select More and then click on “Run as a different user”, it will pop up a credential box.
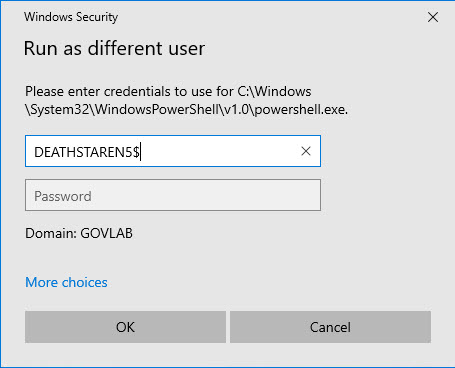
Enter in the gMSA account name and click OK.
You will immediately get an error. This is because Active Directly manages the account for you, so we have no way of knowing what the password is for the account.
There is a utility that will allow us to get around this problem. It is called PsExec and it is a free download from Windows SysInternals.
https://docs.microsoft.com/en-us/sysinternals/downloads/psexec
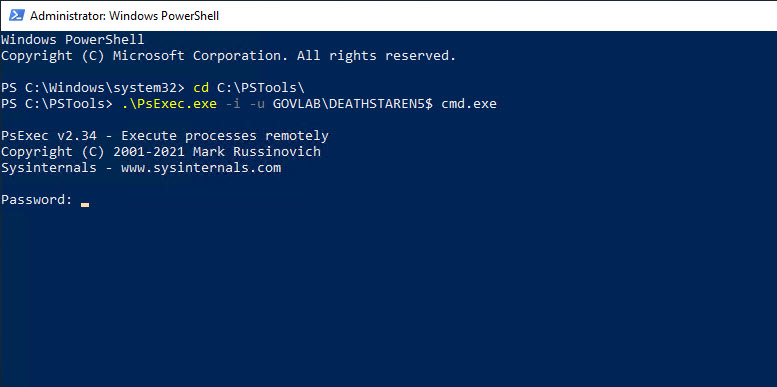
Once you download the utility, uncompress the ZIP into a folder on the server. Next, we need to open a PowerShell window as administrator, change to the folder that contains PsExec.exe, and run the following command. The option “-u GOVLAB\DEATHSTAREN5$” specifies the name of our gMSA and “cmd.exe” is the name of the program we are going to run using those credentials. The “-i” option allows for the session to be interactive with the desktop.
.\PsExec.exe -i -u GOVLAB\DEATHSTAREN5$ cmd.exe
At this point you will get prompted to enter a password. Leave this blank and just hit Enter to continue. A new Command Prompt window will open and be running under the gMSA credentials.
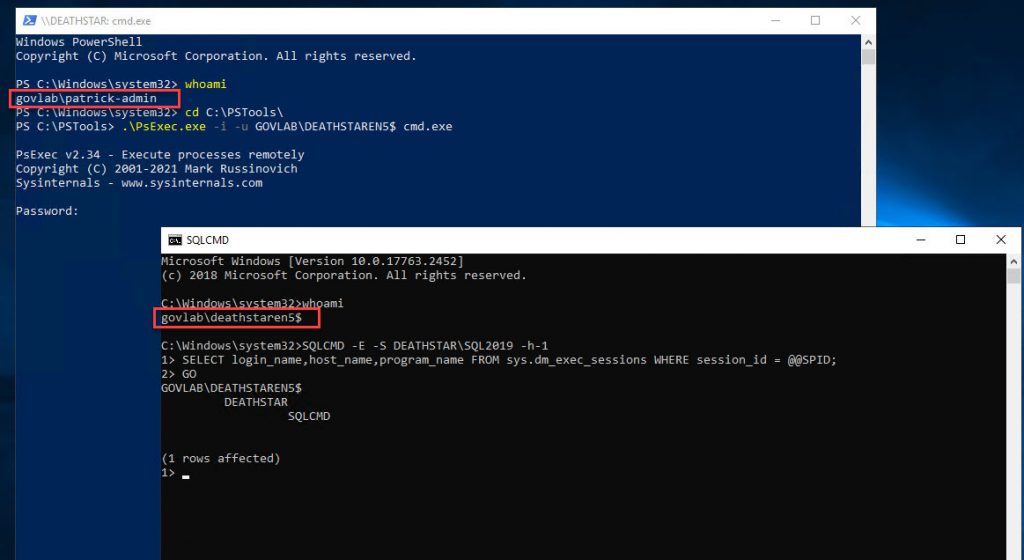
In the following screenshot, I opened the PowerShell window and ran “whoami” to show my current credentials. Then I used PsExec to open a Command Prompt as a gMSA account. Then I ran “whoami” again to show to show I am now running under different credentials. For good measure, I also ran a TSQL command using SQLCMD to doublecheck my credentials.
This example demonstrated how you can open a Command Prompt as a gMSA, but you can specify any other program that you may need for testing; for example, Management Studio.

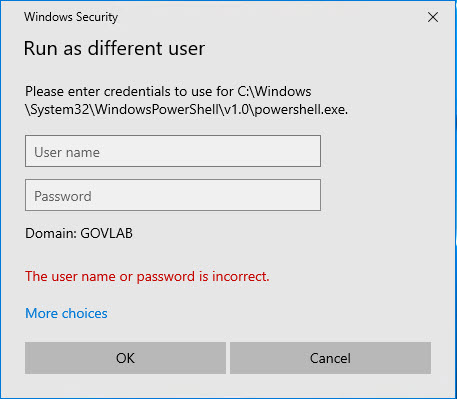



did not work for me. I tried a MSA not gMSA. I got the user name or password is incorrect.
It should work for both MSA & gMSA accounts. Verify the MSA has been properly installed on that server by running Test-ADServiceAccount.
https://learn.microsoft.com/en-us/powershell/module/activedirectory/test-adserviceaccount
In order to get this access I needed to update the command to open the command promt from:
.\PsExec.exe -i -u «DOMAIN»\«gMSA Account Name»$ cmd.exe
…to:
.\PsExec.exe -i -u «SamAccountName»$ cmd.exe
If you do not know your SamAccountName, it is generally the first 15 characters of the account name.
For what it is worth, I am operating on the Server 2022 OS.