In a few previous articles, I have talked a lot about Managed Service Accounts (MSA) and Service Principal Names (SPN) and given examples of managing the separately. As a DBA prepping for a new SQL Server installation, you most likely already know the MSA account name(s) and what is needed to create the associated SPN, so why not create them at the same time? This example uses the PowerShell cmdlet New-ADServiceAccount to create both in the same command. The ServicePrincipalNames parameter can accept an array of strings, so just specify each SPN separated by a comma. We can even run...
Continue reading...Managed Service Accounts
How to Logon Interactively with a Group Managed Service Account
Managed Service Accounts (MSA) are intended to run as a service and not to be used by an end user to logon interactively; however, there are some cases where it is necessary for troubleshooting. From the Start Menu, if you right click on the PowerShell icon, select More and then click on “Run as a different user”, it will pop up a credential box. Enter in the gMSA account name and click OK. You will immediately get an error. This is because Active Directly manages the account for you, so we have no way of knowing what the password is...
Continue reading...Setup Resource-Based Kerberos Constrained Delegation for Group Managed Service Accounts
In my previous post, I discussed how to setup Kerberos constrained delegation and a limitation of using that method. This post will discuss how we can used resource-based Kerberos constrained delegation to do the same thing. Resource-based KCD was introduced in Windows Server 2012, and is defined as… Windows Server 2012 and later gives service administrators the ability to configure constrained delegation for their service. This model is known as resource-based KCD. With this approach, the back-end service administrator can allow or deny specific front-end services from using KCD. Kerberos Constrained Delegation Overview | Microsoft Docs Our environment will be...
Continue reading...Is There a Limit to msDS-AllowedToDelegateTo
For those of you that need to setup Kerberos constrained delegation for Group Managed Service Accounts, you will likely get more familiar with msDS-AllowedToDelegateTo. This attribute stores a list of SPNs that are used to configure a service so that it can obtain tickets used for constrained delegation. In my previous post on setting up Kerberos constrained delegation, I walked you through how we used it to overcome the authenticaiton double hop issue. In that example, we needed to define which SQL Servers the PowerBI Report Server was able to delegate permisisons to. The command below demonstrates how we did...
Continue reading...Setup Kerberos Constrained Delegation for Group Managed Service Accounts
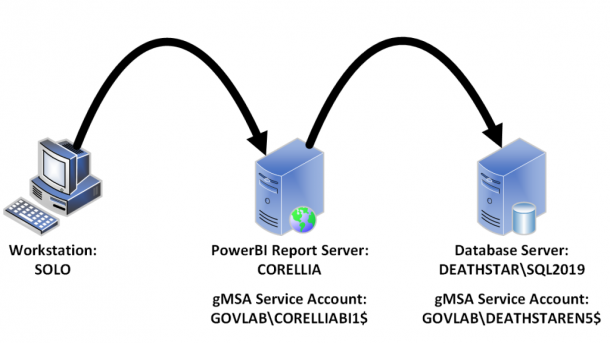
Kerberos delegation is not a new concept in Active Directory; however, setting it up for Group Managed Service Accounts (gMSA) can be a bit confusing. Unlike normal domain accounts, gMSAs do not have a GUI for configuring delegation. Those configuraitons will need to be handled through PowerShell. A common use for Kerberos delegation is to solve the authentication double hop. For example, a user accesses a report which is configured to use a remote data source. That’s one hop from the user’s workstation to the webserver and then a second hop from the webserver to the data source. Our environment...
Continue reading...